Digital malcontents and criminals are running amok — why? Because a heist, if properly pulled off, can lead to huge rewards.
And given the myriad jurisdictional landmines, getting caught, let alone prosecuted, is almost impossible.
A business in London can be targeted by a ransomware attack being orchestrated out of a shack in Belarus.
If the hackers manage to pull it off, they can skim from that London business a rather large sum of money.
If they somehow get ensnared, the chances that the London business will be able to pursue them, on foreign soil, under a foreign regime’s protection – in most cases – is a pipe dream.
That’s why business leaders need to understand the importance of application security testing and the various types available. They are your only line of defense.
Application security testing is a crucial component since it aids in shielding apps and software from potential security threats and vulnerabilities.
It ensures that applications are secure and able to withstand any attempts to compromise them.
Post Contents
- 1 What Is Application Security Testing?
- 2 The Rising Threats In The Cyber World
- 3 How Application Security Testing Can Prevent These Attacks?
- 4 Types Of Application Security Testing
- 5 How To Choose The Right Application Security Testing For Your Business?
- 6 Strategies For Integrating Multiple Types Of Application Security Testing
What Is Application Security Testing?
Application security testing is a procedure for assessing the security posture of an application, locating vulnerabilities, and reducing any potential dangers — the name sort of says it all.
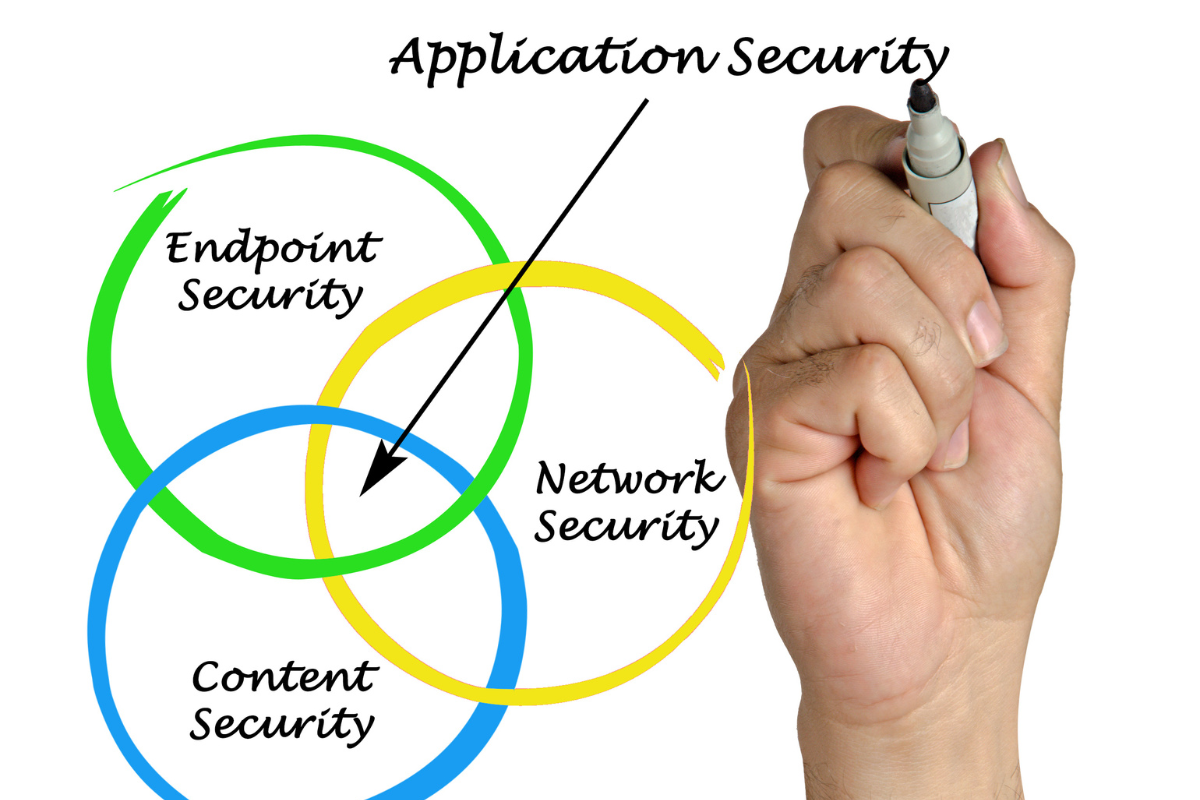
Tests, analyses, and reports that are a part of the security testing process can be used to establish the level of fortification of a software program.
This digital litmus test is important for modern businesses, as it helps ensure that applications are secure and protected from any malicious attacks.
Furthermore, it can help identify any potential areas of risk and address them before the application is deployed — your apps are at the mercy of human error and human hubris.
In many cases, a glitch or bug can be easily laid, when it comes to its creation, on the doorsteps of a coder who simply didn’t have time to double-check their security posture.
The Rising Threats In The Cyber World
The threats to our online security are growing as the cyber world becomes more complicated.
Hackers, in order to steal critical information, use phishing emails, spyware, ransomware, and other dangerous techniques.
Not only that, but they are well funded — even more than you and your staff. They have the latest tech, the most cutting-edge gadgets, and the coolest toys available.
Lone gone are the days of the solitary hacker, the lone gun — today hackers are groups with a business mindset.
They have goals, KPIs, and part of what they earn from a multimillion-dollar score they reinvest back into the business.
In essence, they scale up their criminal empire so they can reach a wider target pool with more ease.
Enterprises and individuals must take into account the liabilities and be cautious in protecting their data and systems.
Implementing strong passwords, regularly updating software, and monitoring networks for suspicious activities may keep potential threats away.
How Application Security Testing Can Prevent These Attacks?
Application security testing ensures that a soon-to-launch or already-on-the-market digital product is safe from any potential threats and that sensitive data is protected.
How does it manage this?
Prevents Malware Attacks
Cross-site scripting, remote code execution, SQL injection, and buffer overflows are some of the errors that can be fixed through the use of application security testing.

Designs A Secure Application
A well-designed application – with true fortification and a shift-left mentality at its core – can be achieved through the use of application security testing.
As a result, the application is continually evaluated for security issues and practical and wile-tested coding techniques are used when writing the code.
Creates and Maintains Secure Software Development Policies
Creates secure development protocols and best practices to ensure the software is tight and compliant with industry standards. It creates a guideline and rulebook by which your organization has to live and die.
Conducts Audits
Runs security audits to assess the overall security posture of the organization.
Applies Security Measures
Application security testing reviews and recommends security measures such as encryption, two-factor authentication, and other security best practices.
Types Of Application Security Testing
There are various types of application security testing that can help avoid breaches. Here are some of them:
Static Application Security Testing – SAST
It is a type of security testing that is done before the application is deployed. It is used to identify any security vulnerabilities by analyzing the source code for any common coding errors.
Mobile Application Security Testing – MAS
This type scans mobile application code for mobile-specific vulnerabilities — such as jailbreaking, device rooting, spoof Wi-Fi connections, certificate validation, and data leakage avoidance.
Dynamic Application Security Testing – DAST
This security testing mode occurs after the application is deployed. It is used to identify security vulnerabilities by analyzing the application while it is running. While they are out in the open in a dynamic and highly evolving ambiance.
Interactive Application Security Testing -IAST
This MO combines the strengths of both dynamic and static security testing to identify security vulnerabilities while the application is running and provides more accurate results than either of the other two methods. It’s a longer and more detailed methodology.
Penetration Testing
Penetration testing is used to identify weaknesses in the system’s security architecture. To do this, a system assault is simulated, and the results are examined for any potential vulnerabilities.
Software Composition Analysis – SCA
This is a type of security testing that is used to identify third-party components in a system.
SCA scans the system for any external libraries, components, or dependencies and then compares them against a known list of vulnerable components.
It’s critical given that today’s applications are wild chimeras — each composed from different source codes, and APIs.

How To Choose The Right Application Security Testing For Your Business?
When selecting an application security testing type for your business, several factors should be considered:
- The scope of the application that needs testing should be your first priority: This will determine which type of security testing is most appropriate. For instance, web application security testing is the ideal choice if the program is web-based or the cloud. On the other hand, mobile security testing is the ideal option if the application is a mobile app.
- Consider the security needs of the application: This will enable you to decide the most suitable security testing method. For instance, vulnerability scanning is the best choice if the program needs to be checked for dynamic vulnerabilities in the code. Or if your app is based on free source code, we would highly recumbent SCA.
- Consider the budget for security testing: Different types of security testing can have different price points, so it is important to consider the budget when selecting a security testing type. For example, automated security testing can be more cost-effective than manual security testing but may not provide the same level of accuracy.
Strategies For Integrating Multiple Types Of Application Security Testing
Integrating multiple types of application security testing can be accomplished by utilizing various strategies.
The first strategy is to use a combination of static and dynamic application security testing – SAST and DAST.
SAST involves analyzing source code for potential security vulnerabilities, while DAST involves testing applications at runtime by simulating an attacker.
By combining the two, organizations can gain a comprehensive understanding of the security posture of their applications.
Another strategy – or attack procedure – involves using a combination of manual and automated testing.
Manual testing allows for more in-depth security testing, while automated testing provides more comprehensive testing coverage.
A third and final strategy is to use a combination of penetration testing and application security testing.
Penetration testing involves attempting to exploit an application to identify security vulnerabilities, while application security testing involves identifying and addressing potential security issues within the code.