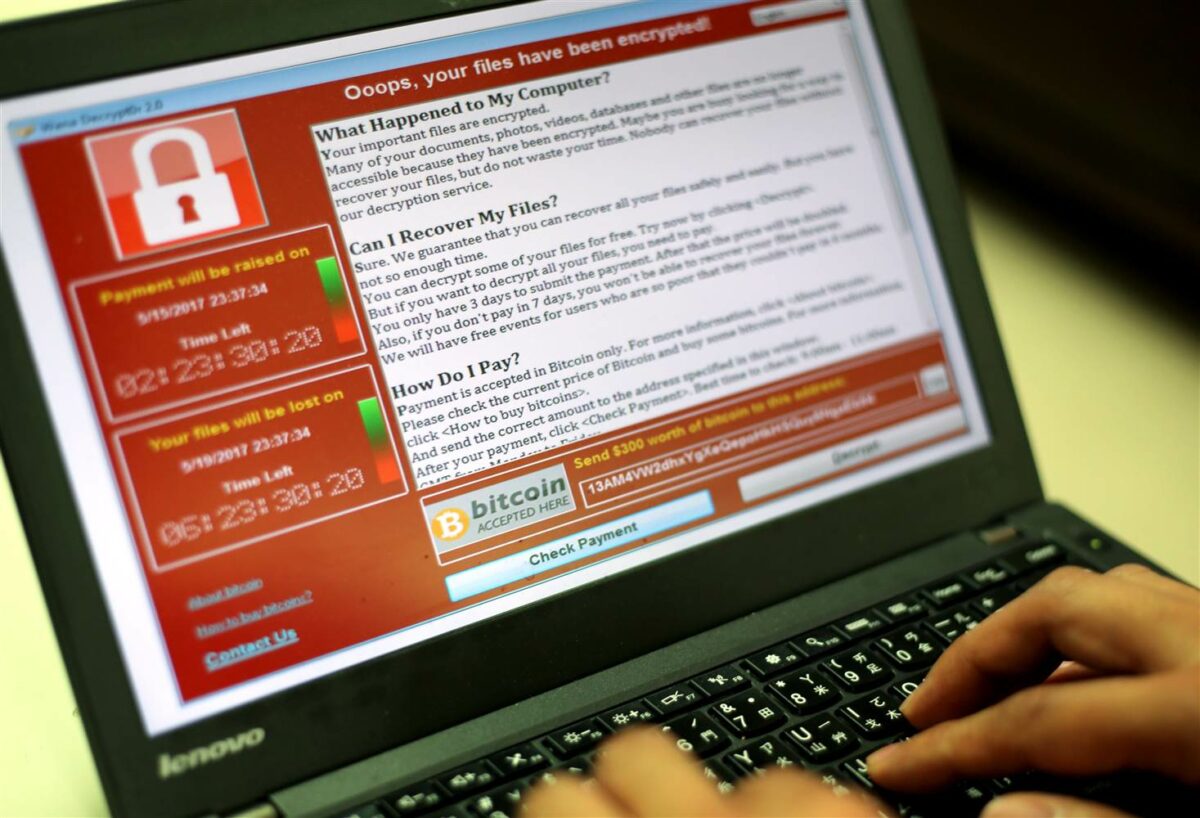
It was just one month ago that the malicious computer worm WannaCry began spreading around the globe.
It was a vicious attack that appears to have been powered by a stolen US cyber weapon and then deployed by a hacking unit in North Korea. In total, the malware locked up between one and two million computers around the world.
Post Contents
200 Countries Affected
The attack affected computers in nearly 200 countries, hitting Russia, China and India the hardest, until a British researcher accidentally discovered a “kill switch” embedded in the WannaCry ransomware. This discovery kept the virus from encrypting upwards of 10 to 15 million computers, according to cyber security experts.
When affected by the worm, a computer would display a ransom message on its screen that demanded payment of $300 in bitcoin, a digital currency, in order to be able to access the hard drive.
North Korea to blame
This week, the Trump administration in Washington laid formal blame for WannaCry on “cyber actors of the North Korean government.”
In a combined alert issued Tuesday by the US Department of Homeland Security and the FBI, a North Korean hacking unit called the Lazarus Group was specifically named as the perpetrators of the virus. This conclusion agreed with the observations of several private cyber security firms who had also reported that North Korea appeared to be the origination of the malware.
The most notable previous attack by the Lazarus Group was a 2014 breach that occurred when Sony Pictures was hacked resulting in the delayed release of a satirical movie, “The Interview,” that portrayed an assassination attempt on President Kim Jong Un of North Korea.
Another attack in 2016 in Bangladesh resulted in the loss of approximately $80 million from the Bangladesh Central Bank has also been blamed on the group.
Damage could have been much higher
Researchers say that the WannaCry epidemic appears to have infected between 240,000 to 300,000 computers around the world. But the actual damage could have been far higher.
Variants of original worm were designed to infect up to seven million computers in the US but were stopped by a “kill switch” that was activated by a British blogger MalwareTech who noticed that the ransomware’s code connected to an unregistered domain name.
His company tracks botnets by registering unregistered domains and, as luck would have it, once the domain was registered, the worm was terminated.
According to reports, the kill switch was written into the malware so that the creator would have a way to stop it from spreading. The process involves the malware making a request to the domain name and if that request comes back showing that the domain is live, then the kill switch is activated and the malware stops spreading.
A wakeup call
The WannaCry ransomware was a wakeup call that should not be ignored. Even though the virus got lots of public attention, it did not generate much profit for the cyber-criminals that launched it.
The next attack is coming. Get support from a third party. Make your backups regularly, and be prepared.